This is a quick guide on how to configure to open nsupdate with a configured tsigkey stored in KeePass. nsupdate is used to submit Dynamic DNS Update requests as defined in RFC2136 to a name server. This is useful when administrating a dynamically managed DNS zones. To secure the process i.e. allow it to be done from an administrators computer the transaction is a authenticated with the use of TSIG, however specifics about TSIG, nsupdate and DNS in general are not the goal of this post.
As I didn’t want my personalized TSIG key lying around in a directory somewhere on my computer I instead put it in KeePass. And as I also didn’t want to copy it into the nsupdate interactive shell each time a created a quick URL Override for KeePass to do it for me.
Prerequisites
First of you need a locally installed instance of nsupdate. On my Windows 10 I used Windows Subsystem for Linux (WSL) to install ns
update via APT apt update; apt install -y dnsutils. Alternatively you can download the Bind9 package for Windows from
ISC and extract nsupdate.exe from there.
KeePass configuration
To change the default URL action for a URL scheme (e.g. https:// or ftp://), got to Tools -> Options -> tab Integration ->
URL Overrides and define a new URL scheme override.
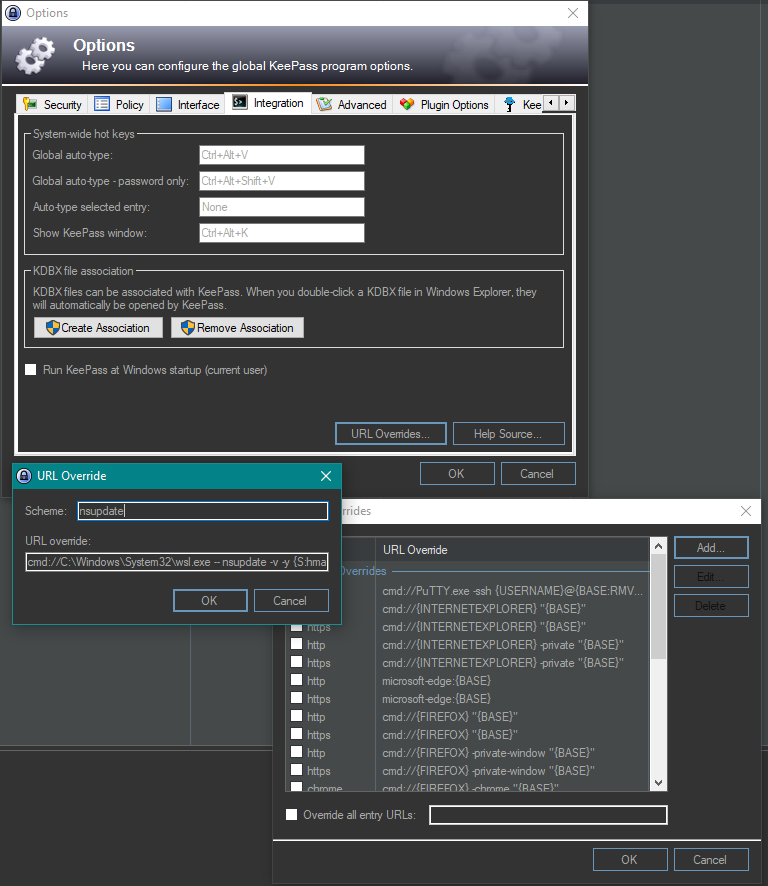
Scheme: nsupdate
URL override: cmd://C:\Windows\System32\wsl.exe -- nsupdate -v -y {S:hmac}{USERNAME}:{PASSWORD}
Or if you downloaded nsupdate.exe:
URL override: cmd://C:\<path>\<to>\nsupdate.exe -v -y {S:hmac}{USERNAME}:{PASSWORD}
After creating the URL override you can trigger the shell from a entry with a nsupdate:/// url entry. The entry uses the usernames
as key name and the password as the base64 encoded secret key as found in the .private file.
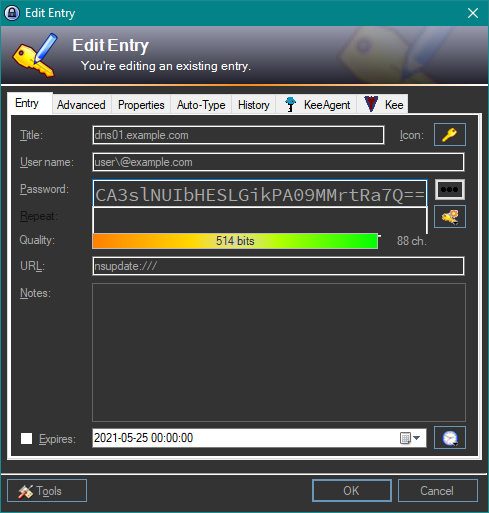
If you use a key algorithm other than HMAC-MD5 (and you should), then you need to also define the custom string field hmac for
the entry. This field is used to tell nsupdate what key algorithm is in use for the key.
Important this value has to end in : es
it is seen as part of the key name.

Possible key algorithms:
hmac-md5hmac-sha1hmac-sha256hmac-sha512